This has been described as similar to the nmap command when passed the -sS flag. As long as intervening routers will pass the packet, the trace will work. If revealing a few internal IP addresses is a major issue, then this means that your network is doomed. IP addresses are not meant to be secret and are rather easy to obtain for attackers through various means mass scanning comes to mind, but also searching garbage bags for printouts of network maps -- the modern fashion of recycling makes dumpster diving a much easier and cleaner activity than what it used to be. Sign up using Facebook. Correspondingly, many sysadmins consider traceroute as a serious breach, to be fixed and blocked as soon as possible. In this case, it doesn't appear you have anything to gain. 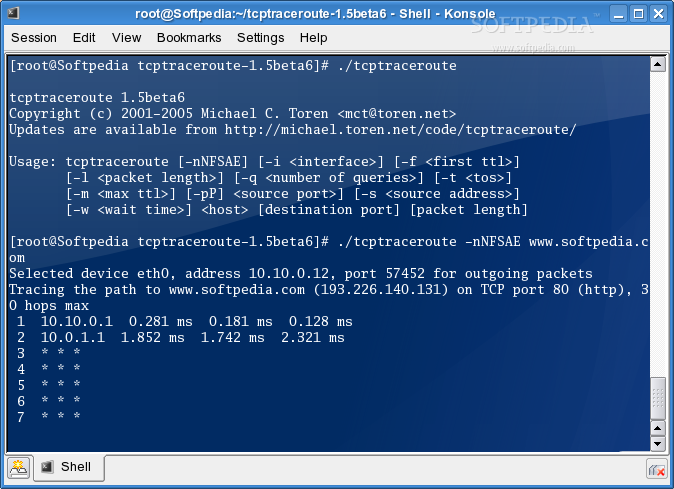
| Uploader: | Araran |
| Date Added: | 18 May 2004 |
| File Size: | 43.88 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 7139 |
| Price: | Free* [*Free Regsitration Required] |
But again, the destination server is the least important. There is nothing to mitigate.
Both traceroute and tcptraceroute work on the same basic principle: How can this be mitigated? However, it won't perform a traceroute in and of itself; you need to combine it with the --traceroute option and then I think you're still scanning, not just performing a traceroute, so if you want tvptraceroute trace I tcptraceroutf tcptraceroute or traceroute -T if your OS supports it. Improving the question-asking experience. However, blocking such packets tend to break the Internet because hosts adaptively change the TTL in the packets they send in order to cope with long network paths, and they need these ICMP for this processso, on a general basis, the "Time Exceeded" ICMP packets are not blocked.
Granted, having precise and extensive knowledge of tcphraceroute network infrastructure can only help attackers; but not in really significant amounts. How do we handle problem users?
Of course, you could always unplug your server, that'll mitigate all sorts of stuff. IP addresses are not meant to be secret and are rather tcptraxeroute to obtain for attackers through various means mass scanning comes to mind, but also searching garbage bags for printouts of network maps -- the modern fashion of recycling makes dumpster diving a much easier and cleaner activity than what it used to be.
Take a web site like amazon. The best answers are voted up and rise to the top.
This has been described as similar to the nmap command when passed the -sS flag. In this case, it doesn't appear you have anything to gain.
tcptraceroute(1) - Linux man page
If your security depends on keeping this sort of information secret, then you should sit down and reconsider the decisions that got you here. Asked 6 years, 2 months ago. The only gcptraceroute you might miss is a response from the final destination host, but with traceroute that is the least important response, since what traceroute provides you is the list of intermediate routers.
However, a relatively widespread myth is that keeping your addresses secret somehow ensures security. The former is why tcpteaceroute has become more popular; any site that allows connectivity on at least one TCP port - like a web site - is permitting packets in.
Article Page
Blocking ICMP responses has the side effect of breaking necessary IP networking fundamentals, which ycptraceroute from mildly impolite to wildly counterproductive. Sign up using Email and Password.
That kind of packet is not usually blocked by firewall, at least as long as the destination port is "allowed". By using our site, you acknowledge that you have read and understand our Cookie PolicyPrivacy Policyand our Terms of Service.
Thomas Pornin Thomas Pornin k 52 52 gold badges silver badges bronze badges. Information Security Stack Exchange is a question and answer site for information security tcptraceroutd.
If this is accurate, what does it actually mean? All the tracerouting tools rely on the following principle: Sign up to join this community.
How to run a TCP Traceroute
Note that whether or not ICMP is allowed on the destination server is entirely irrelevant as it is the intermediate routers that are returning the Time Exceeded responses. What information can be disclosed or other risks? Home Questions Tags Users Unanswered. Traceroute can be mitigated by not permitting packets in or by blocking ICMP responses back.
Traditional traceroute uses ICMP echo requests, but this is just by convention. Worrying about secrecy of IP addresses is like triggering a major incident response plan because an outsider learned the menu at the company's cafeteria. Active 6 years, 2 months ago. Unicorn Meta Zoo 9:


Комментариев нет:
Отправить комментарий